An Overview of AWS VPC Networking
Recently, my work requires me to familiarize myself with concepts such as AWS Availability Zones, subnets, network connectivity, NAT Gateways, and Internet Gateways. I would like to summarize my understanding of these topics briefly.

Concepts
VPC (Virtual Private Cloud)
VPC is a virtual network service in Amazon Web Services (AWS) that allows you to create your own private network within the AWS cloud. With VPC, you can run your AWS resources in a private and customizable logical network, including custom IP address ranges, subnets, route tables, and network access control lists. This enables your applications or services to operate securely and in a controlled manner in the cloud.
Availability Zones
Availability Zones are separate data centers within an AWS geographical region. AWS infrastructure is distributed across these Availability Zones, and they are designed to provide high availability and fault tolerance. Availability Zones are interconnected through low-latency networks. By distributing resources across multiple Availability Zones, you can increase the availability of your applications and have disaster recovery capabilities in place.
Subnet
A subnet is a range of IP addresses within your VPC. You can create AWS resources, such as EC2 instances, in specific subnets. Each subnet must be completely contained within a single Availability Zone and cannot extend across multiple zones.
The subnet type is determined by how you configure routing for your subnets. For example:
- Public subnet – The subnet has a direct route to an Internet Gateway. Resources in a public subnet can access the public internet.
- Private subnet – The subnet does not have a direct route to an Internet Gateway. Resources in a private subnet require a NAT device to access the public internet.
- VPN-only subnet – The subnet has a route to a Site-to-Site VPN connection through a virtual private gateway. The subnet does not have a route to an Internet Gateway.
- Isolated subnet – The subnet has no routes to destinations outside its VPC. Resources in an isolated subnet can only access or be accessed by other resources in the same VPC.
NAT(Network Address Transalation) gateways
NAT Gateways are associated with a specific subnet within your VPC.
They allow instances in a private subnet to connect to services outside the VPC, while preventing external services from initiating connections with those instances. NAT Gateways provide outbound internet connectivity for resources in a private subnet by performing source network address translation (SNAT). This translates the private IP addresses of the instances to the public IP address assigned to the NAT Gateway, enabling them to access the internet securely while hiding their private IP addresses. NAT Gateways can be categorized into two connectivity types: public and private.
Internet Gateways
The Internet Gateway (IGW) is a scalable and redundant component of a VPC, allowing communication between the VPC and the internet. It enables resources in public subnets to connect to the internet and allows internet-based resources to reach your subnet. Without an IGW, VPC resources can only be accessed via a corporate network and VPN/Direct Connect. IGW supports both IPv4 and IPv6 traffic and doesn't impose availability risks or bandwidth constraints. To make a subnet public, add a route to the subnet's route table directing internet-bound traffic to the IGW.
A VPC can have only one associated IGW, which is not tied to a specific Availability Zone.
Route table
A route table contains a set of rules, called routes, that determine where network traffic from your subnet or gateway is directed. See Configure route tables for more details about configuration.
Example
The diagram below illustrates a typical deployment pattern of NAT Gateways, Internet Gateways, and subnets within an AWS VPC.
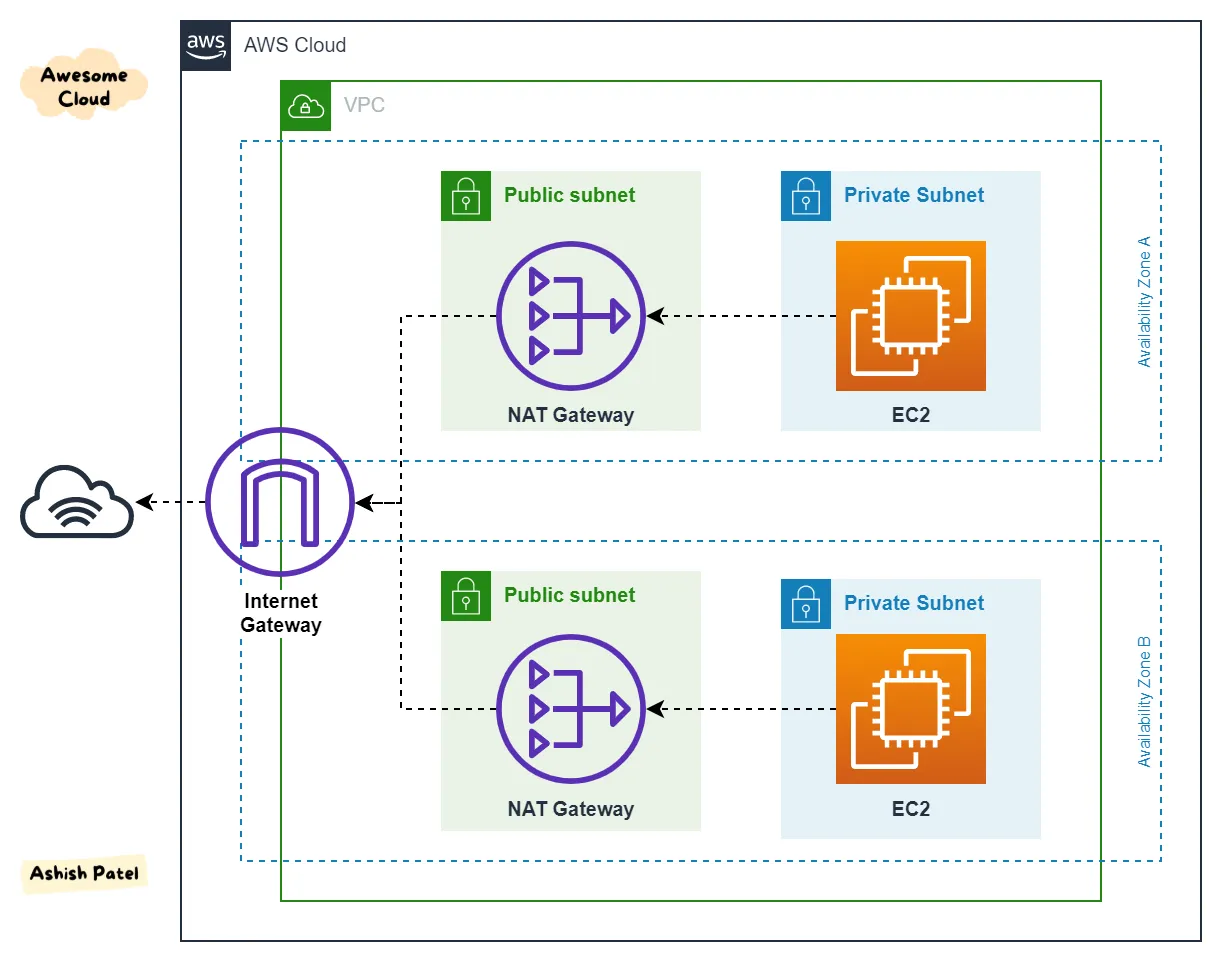
First, we create a VPC. As we have a requirement to access the internet within the VPC, we definitely need an Internet Gateway (IGW).
Next, there will be EC2 instances that need to communicate with the IGW through a route table. Consequently, the subnet in which these EC2 instances reside will be a public subnet. At this point, considering security concerns, there will definitely be a need to establish a private subnet. More machines will be placed in the private subnet, and if these machines require internet access, routes to the NAT Gateway in the public subnet will need to be set up in the route table.
In order to achieve high availability across multiple availability zones, we might use multiple availability zones. The diagram above illustrates a scenario where machines in the private subnet access the internet through the NAT Gateway in the public subnet with the help of the IGW via two routing hops.